How to disable the Comodo reseller root certificate in Firefox
Slashdot is a-buzz (and rightly so!) with news that people have been able to obtain an SSL certificate for a domain they don’t own, by applying with one of Comodo’s certificate resellers. It is clear that there has been a major breach of trust, but we’re not sure of the best general solution. There has been a discussion in the mozilla.dev.tech.crypto newsgroup about what steps Mozilla should take for this breach.
In the meantime, I recommend disabling the root certificate used by this certificate authority, to avoid the possibility that other fraudulent certificates are floating around in the wild. Here’s how to disable the relevant CA root in Firefox:
- Open the preferences window
- Select the “Advanced” tab
- Select the “Encryption” sub-tab
- Choose “View Certificates”
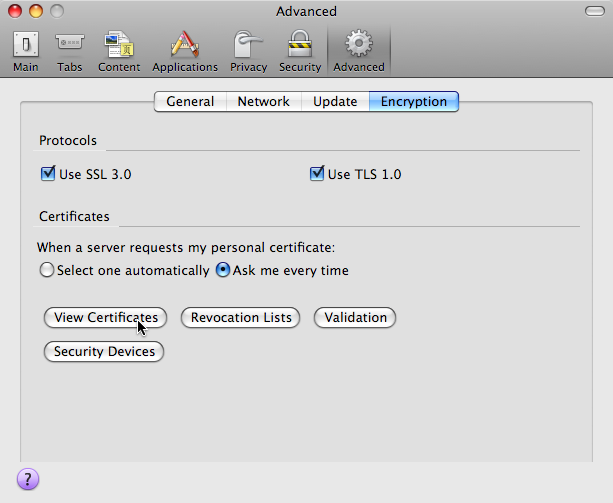
- Find and select the “AddTrust AB / AddTrust External CA Root” item
- Choose the “Edit’ button
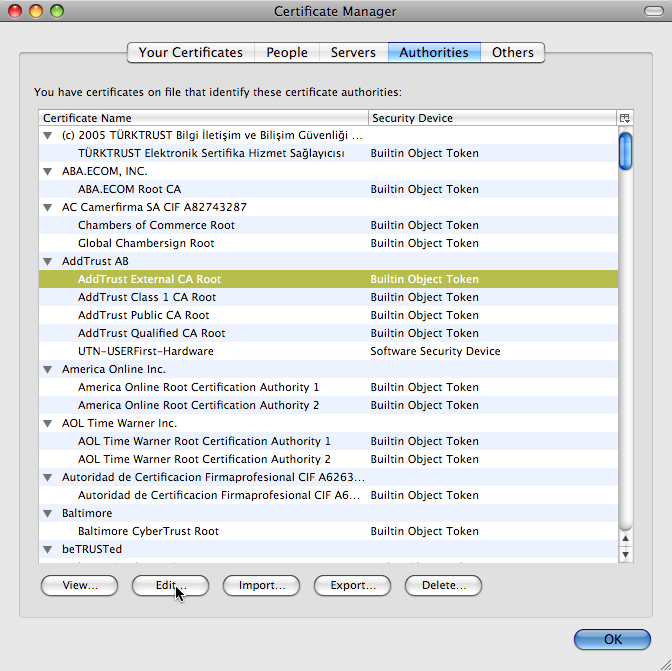
- Remove all trust setting check-boxes.
Note: disabling this root certificate will SSL websites validated by this Comodo reseller to stop working. That’s why you’re doing it, but if it’s your favorite website that stops working, please don’t blame me! If you’re really paranoid, you could also disable all Comodo roots: these include all the certificates with names like “AddTrust”, “Comodo CA Limited”, and “The UserTrust Network”.
Thanks to Eddy Nigg for first providing these instructions.

December 24th, 2008 at 3:27 pm
Thanks! I’m trying to do this in Chrome too, however there are no AddTrust root certificates in Chrome it seems. So I guess Chrome users are already good. :) Unless AddTrust is covered by the COMODO root cerficiate, which is present in Chrome.
December 24th, 2008 at 3:29 pm
Hmm… looks like Chrome just uses Microsoft’s Root Certificates. When you go to manage the certificates it just pops open the Internet Options dialog for it.
December 24th, 2008 at 9:12 pm
[…] Comodo fiasco is pretty depressing. We have a CA Policy that states we’ll might do something in […]
December 24th, 2008 at 9:46 pm
Thanks! The paranoid approach appears to have disabled Expedia.com from being trusted for me (I *think* it uses a UserTrust network certificate).
December 24th, 2008 at 11:05 pm
Hmm… the bogus certificates (as shown in Eddy Nigg’s blog post) were issued under UTN-UserFirst-Hardware, so wouldn’t it be pointless to disable the AddTrust root?
December 27th, 2008 at 12:29 pm
Thank you. I would rather be safe than sorry. I can always use the phone for a few days. I expected this sort of thing to happen. I also expected that Mozilla folks would take the lead on sorting this out. My vote, shut Comdo down. Its the only way these guys will learn
December 30th, 2008 at 1:35 pm
[…] Firefox – The instructions are for the Comodo certificate, but it’s the same thing. […]
December 30th, 2008 at 3:04 pm
[…] Ltd. from the Certstar Comodo reseller, no question asked. Of course, as a work-around, you could remove the offending CA root, but you must expect side effects (I discovered this breaks cleverbridge e-commerce back-ends, for […]
December 31st, 2008 at 2:17 am
[…] Ltd. from the Certstar Comodo reseller, no question asked. Of course, as a work-around, you could remove the offending CA root, but you must expect side effects (I discovered this breaks cleverbridge e-commerce back-ends, for […]
January 2nd, 2009 at 10:30 am
Debian and Ubuntu users can run these commands to quit trusting certificates from Comodo, UserTrust and AddTrust:
sudo sed -ri ‘/comodo|utn|addtrust/Is/^!*/!/’ /etc/ca-certificates.conf; sudo update-ca-certificates
January 4th, 2009 at 11:11 pm
[…] Ltd. from the Certstar Comodo reseller, no question asked. Of course, as a work-around, you could remove the offending CA root, but you must expect side effects (I discovered this breaks cleverbridge e-commerce back-ends, for […]